Ransomware cyber-attack threat escalating – Europol
US President Donald Trump has ordered his homeland security adviser, Tom Bossert, to hold an emergency meeting to assess the threat posed by the global computer ransomware attack.
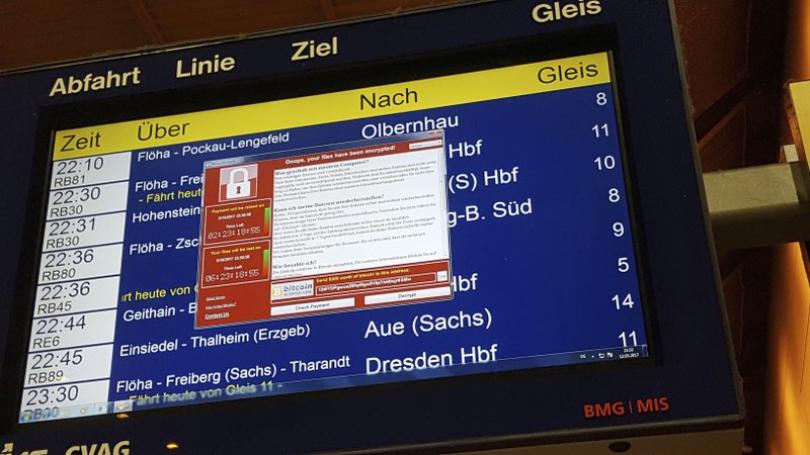
It’s not the first time hackers have used the leaked NSA tools to infect computers. By encrypting files, hackers rendered them unreadable, and demanded $300 in ransom to decode them. That’s why it’s called ransomware.
Around a fifth of trusts were hit amid concerns networks were left vulnerable because they were still using outdated Windows XP software.
The virus spread quickly because the culprits used a digital code believed to have been developed by the US National Security Agency – and subsequently leaked as part of a document dump, according to researchers at the Moscow-based computer security firm Kaspersky Lab. The Shadow Brokers group, which is suspected of having ties to Russian Federation, posted Windows hacking tools last month.
Microsoft released a security patch for the vulnerabilities in March. Many of those victims will be businesses, including large corporations.
An IT worker at the public health care system tells The Guardian newspaper that it’s the biggest problem they’ve seen in their six years working for the service. Playing with fire finally caught up with the victims.
Every States worker has also been sent instructions on how to reduce the risk of an attack.
It comes after more than 200,000 victims in around 150 countries were infected by the ransomware which originated in the United Kingdom and Spain on Friday before spreading around the world.
Some hospitals were forced to cancel procedures and appointments, as ambulances were directed to neighbouring hospitals free from the computer virus.
But while FedEx Corp. reported its Windows computers were “experiencing interference” from malware-it wouldn’t say if it had been hit by the ransomware-other impacts in the U.S. were not readily apparent last Saturday.
Companies and institutions are often slow to update their computers because it can screw up internal software that is built to work with a certain version of Windows.
Cyber security experts say the spread of the virus dubbed WannaCry – “ransomware” which locked up computers in auto factories, hospitals, shops and schools in several countries – has slowed, but that any respite might be brief. Most importantly, such a convention would commit governments to turning over software vulnerabilities when they find them – rather than exploiting them to break into enemy computers – so that companies can patch them.
Such ransomware attacks are commonplace, with an estimated 600 million attacks likely recorded in 2016 alone. The NHS said on May 13 that nearly all of its computers were back to normal operation.
When a system has been infected with WannaCrypt, the malware encrypts everything it can – including the PC’s hard drive and any connected devices, such as USB sticks and external storage devices. Install all Windows updates. 5. The hackers here weren’t playing some political interference game: They were after money, in bitcoin.
The researcher tweeted that he initially didn’t know that his actions would stop the malware.
On Saturday, experts said it appeared that the ransomware had made just over $20,000, although they expected that number to pop when people went back into the office Monday. MalwareTech said in a blog post last Saturday he had returned from lunch with a friend last Friday and learned that networks across Britain’s health system had been hit by ransomware, tipping him off that “this was something big”.
“A lot of people are going to go to work on Monday and click on a link in their mail – completely oblivious that all of this is going on or have heard about it and think that it’s over – and suddenly wipe out their whole company”, Gazeley said from Hong Kong.
Cyber security experts are still scrambling to contain a global ransomware attack that has infected tens of thousands of computers in almost 100 countries, including the U.S., U.K., Russia, China, Ukraine, and India. Meanwhile, the malware was able to spread widely through university, business and government networks.