Frenchmen claim cure for WannaCry-infected computers
Wannacry spread so quickly in 24 hours due to the lack of proper security practices in place in organisations, and new versions of it are already online.
Much of the growth will be spurred by massive cyber attacks like the so-called “Wannacry” ransomware that struck targets in dozens of countries, ranging from British hospitals to Russian banks.
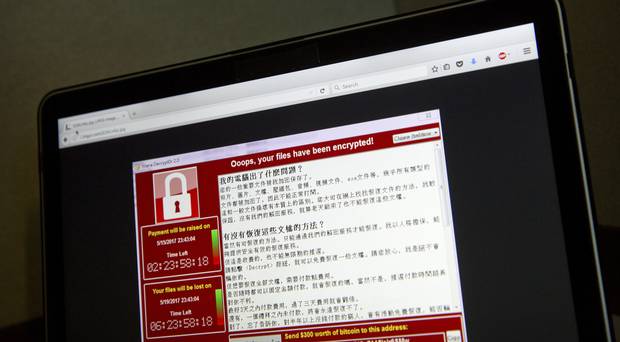
Security researchers have released a fix to get rid of the ransomware, given you haven’t rebooted your computer yet.
Paris-based Adrien Guinet, who works for the IT security company Quarkslab, developed a theoretical technique for decrypting the files blocked by WannaCry. Using those prime numbers it then generates unlock keys for the encrypted files. They are said to “mine” for the currency and are occasionally rewarded with a piece of it. Once the issue became widespread and the news and views cycle went on an overdrive, it was surprising to see Microsoft getting the heat for not supporting Windows XP.
Information technology professionals should also regularly educate and test employees on spotting suspicious emails, said Mr Matt Ahrens, vice president of Crypsis, a cybersecurity firm. They allege that last week’s WannaCry attack exploited a flaw that the USA government knew about and chose not to disclose, an identical situation to the Heartbleed virus that the National Security Administration knew about for around two years before researchers discovered it and announced it to the public. Police say India too was affected, and anti-virus companies have observed 48,000 attacks here. Brad Smith, Microsoft’s top lawyer, criticized US intelligence agencies for “stockpiling” software code that can be used by hackers.
A former U.S. government official said that while Microsoft had significantly improved its security over the past 10 to15 years, it could have acted to protect Windows XP before the ransomware crisis.
The attack has reportedly hit 74 countries including the United Kingdom, U.S., China, Russia, Spain, Italy and Taiwan.
IT Security providers, including ESET, offer specialized products like ESET Threat Intelligence, which equip companies with the deeper information needed to better defend themselves against targeted attacks and ransomware threats like WannaCry in a timely manner. Lucifer did strike past year which locked computers of banks and pharmaceutical companies.
The key is to minimise the risk and make it more hard for cyber criminals to compromise systems. In January, another ransomware by the name of Lazarus had attacked Indian companies. This weekend’s virus was particularly virulent, because it could spread to all other computers on a network even if just one user clicked a bad link or attachment.
A wake up call for businesses? Yet in an unusual step, they released a patch for those older systems because of the magnitude of the outbreak.
The fight against cyberattacks has sparked exponential growth in global protection spending, with the cyber security market estimated at $120 billion this year, more than 30 times its size just over a decade ago.
The alarming sophistication of ransomware, marks a paradigm shift in the cybersecurity ecosystem. This threat is detected as “Ransom:Win32/WannaCrypt”. For example, in India, most of the systems are not safe from future attacks. Within 24 hours of the attack, a malware researcher had discovered a “kill switch” to stop the unchecked spread of the malware, but he also issued an ominous warning sure to reverberate in the days and weeks to come: “People need to update their systems ASAP!”
Microsoft held back from distributing a free fix for old versions of its software that could have slowed last week’s devastating ransomware attack, charging some customers $US1,000 a year per device for protection against such threats.
Vox also called on the public to update their Windows operating systems to avoid security problems.