How to keep your PC safe from the WannaCry attacks
Hutchins told The Guardian that he bought the domain with the initial intent of monitoring the attack’s deployment patterns but they “actually stopped the spread just by registering the domain”.
This time, though, Microsoft believes others should share responsibility for the attack, an assault that targeted flaws in the Windows operating system.
Brad Smith, the President and Chief Legal Officer of Microsoft has blamed the practice of US’s National Security Agency for developing hacking techniques to use against the own enemies of the USA government, while some others have blamed Microsoft’s poor programming.
While the NHS could have been more responsible, the root of the virus links back to the NSA for failing to report software vulnerabilities to companies so they can be fixed, especially the “Eternal Blue”, which was stolen by the hackers responsible for Friday’s attack.
“This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem”, according to Smith.
“We have seen vulnerabilities stored by the Central Intelligence Agency show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world”, wrote Smith in a blog post on Sunday.
Calling for a “Digital Geneva Convention”, Microsoft’s Smith said the widespread damage caused by the ransomware shows that governments need to treat cyber weapons the same way they treat conventional weapons.
Smith went on to describe the situation as the equivalent of U.S. Tomahawk cruise missiles getting stolen from military stockpiles. This worldwide attack has posed as a wake up call for Microsoft and also led software security providers to amplify anti-malware software.
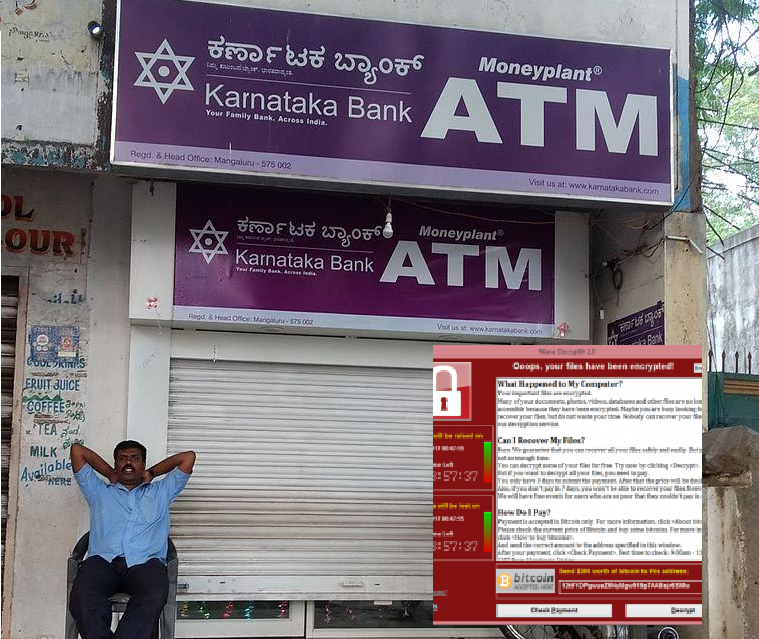
Information on the vulnerability exploited in the WannaCrypt attack (also called WannaCry, Wana Decryptor or WCry) was reportedly stolen from the NSA in April.
Well, a vulnerability first uncovered by the National Security Agency and then released by hackers on the internet is now being used in one of the most prolific cyberattacks ever around the globe.
While the scale of the WannaCry ransomware attack is unprecedented, it could have been much worse.
Security experts warn that while computers at more than 300,000 internet addresses were hit by the ransomware strain, further attacks that fix weaknesses in WannaCry will follow that hit larger numbers of users, with more devastating consequences. “Despite appearing to be criminal activity meant to raise money, it appears that less than $70,000 has been paid in ransoms and we are not aware of payments that have led to any data recovery”. Even as the Centre expressed confidence that WannaCry ransomwarewill have little impact on India, cyber security experts said it is too early to assess the real extent of the virtual attack. The hackers behind WannaCry only accept ransom paid via BitCoin, a digital currency that ensures that the transaction can not be traced.
“There’s no guarantee that when you pay the money that your files will then be decrypted”, said cyber security expert Patrick Siewert.
“The fact that so many computers remained vulnerable two months after the release of a patch illustrates this aspect”. No matter how Microsoft pushes the newest system to customers (the upgrades are free), some systems stick with the old versions, simply because they can’t afford the switching effort in terms of the time required and the old hardware’s insufficiency. Companies including Hitachi and Nissan Motor Co. reported problems but said they said had not seriously affected their business operations.
Soon after the attack became public, Microsoft rushed a security patch for its Windows XP operating system even though it ended support for Windows XP in 2014.
Don’t grumble when your system administrator at work takes the network down periodically to update systems, which usually includes installing new and often critical software patches. Microsoft released a software update in March that protects against this vulnerability, but we’ve since learned that many people did not update their computers.
When Microsoft sells software it does so through a licensing agreement that states the company is not liable for any security breaches, said Michael Scott, a professor at Southwestern Law School.